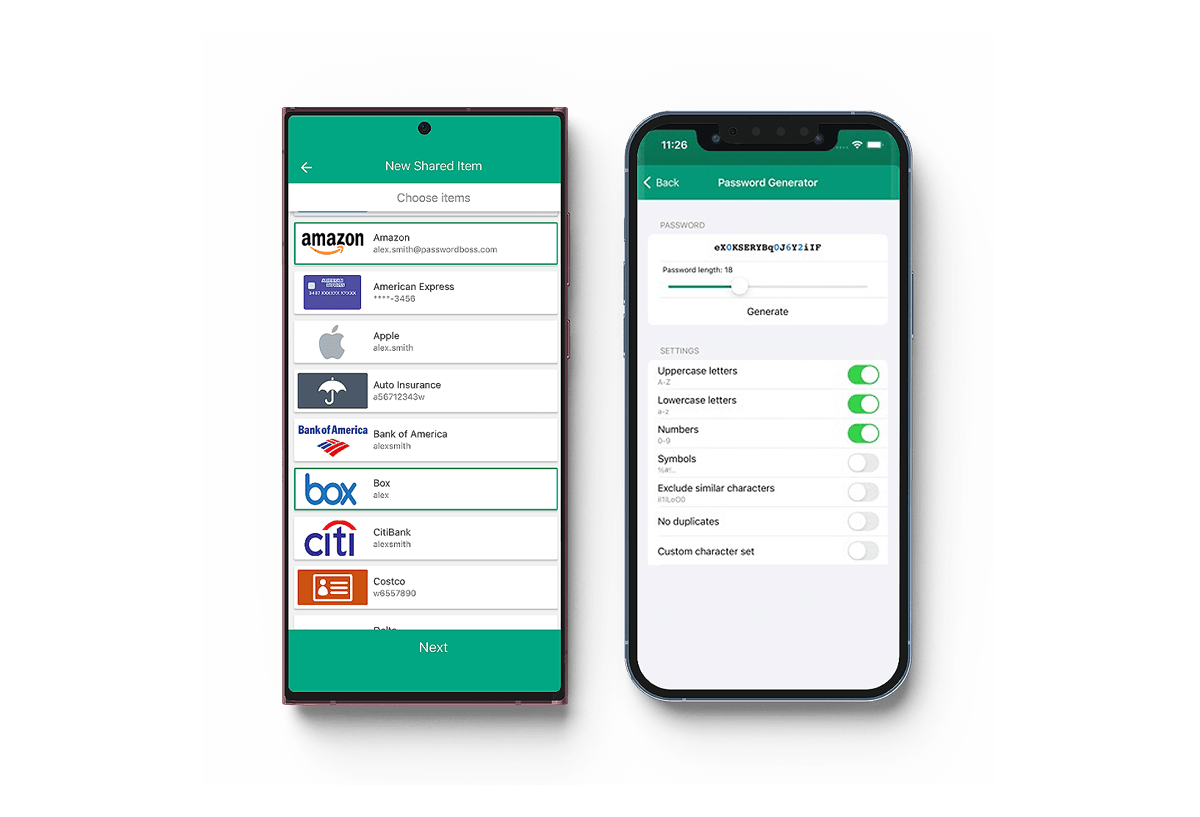
Easy Password Management for MSPs and IT Professionals
Password Boss WebApp allows you to access, share, and secure passwords for end users and customers in one simple, affordable tool.
Password Management, Simplified
Protect Data from Theft
The remote delete function will automatically delete encrypted user data stored on a stolen or misplaced device if someone tries to access the password application.
Securely Share Passwords
Passwords and digital notes are encrypted using 2048 bit RSA key pairs to ensure that no unencrypted data is sent between employees or stored on our servers.
Get Up and Running Fast
Access Passwords from All Devices
Assign roles to team members so they can set up, manage, and access user passwords and notes from any device.
Password Boss WebApp Features
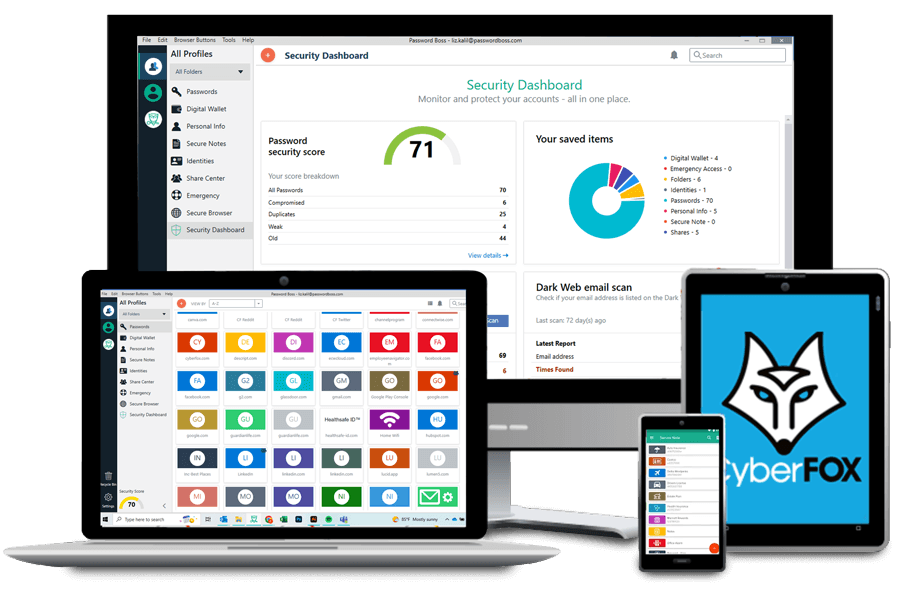
Ensure both stronger security and uninterrupted workflows with the advanced security features of our password management tool.
- End-To-End Encryption
- Enterprise Grade Security
- Secure Cloud Storage
- Role-Based Access
- Advanced Security Policies
- Dedicated Support
See Our Solutions in Action
Ready to see how easy it is to put our advanced cybersecurity solutions to work for you? Start your free trial or schedule your free demonstration today.
In-Depth Cybersecurity Insights
5 DNS filtering myths (that put users at risk)
Despite all of their cybersecurity benefits, DNS filters remain one of the most misunderstood tools in most IT pros’ stacks..
Is your AI talking to strangers? DNS filters can help
Remember when the biggest threat to an organization’s cybersecurity was someone writing their password on a sticky note? Ah, those.

7 ways DNS filtering keeps users safe (and makes your job easier)
DNS filtering is the unsung hero of cybersecurity. It quietly does the hard work of protecting your network while all.

Why DNS filters should be part of your cybersecurity stack
Let’s be honest, most of us don’t think about DNS (Domain Name System) filters until something goes wrong. This behind-the-scenes.

Why MSPs need to offer password management (before clients ask for it)
You’re already your clients’ go-to person for system updates, troubleshooting, new user onboarding, and everything in between. But if you’re.