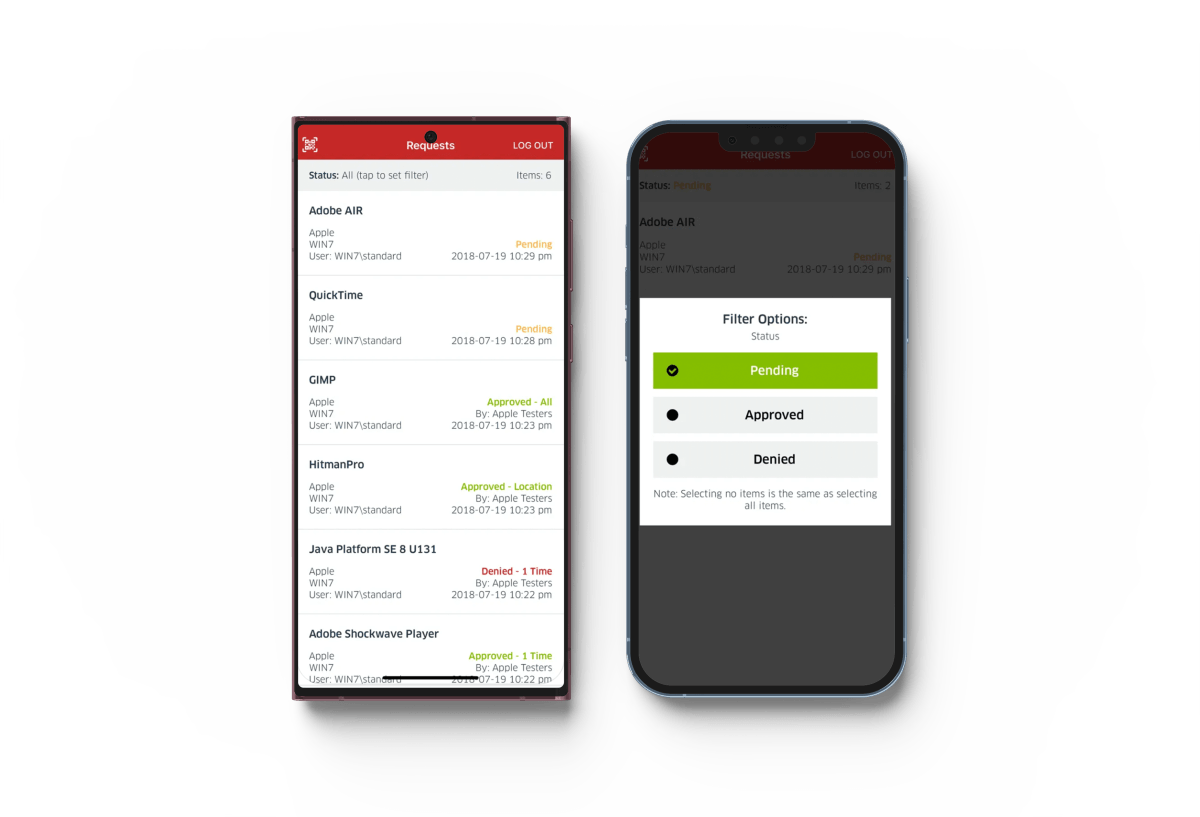
A Simple Privileged Access Management Solution for MSPs and IT Professionals
Our Privileged Access Management (PAM) solution, CyberFOX AutoElevate, allows you to remove local admin rights and secure end users without frustrating or slowing them down.
PAM Made Easy
Reduce Your Threat Factor
Significantly improve security with a PAM tool that helps companies significantly reduce their threat factor.
Manage Privileges Remotely
Securely approve requests, make rules, manage privileges, and more, from anywhere, as needed.
Easily Remove Local Admin Rights
Simpler to Use than Other Solutions
Easily set up the solution, audit events, create rules, and automate ticket requests.
Why Remove Local Admin Rights?
Ready to see how easy it is to put our advanced cybersecurity solutions to work for you? Start your free trial or schedule your free demonstration today.
Meet compliance goals and check the PAM box needed for most cyber insurance coverage.
94% of Microsoft vulnerabilities can be avoided by removing admin rights.
Cybersecurity best practice frameworks like CIS Critical Controls and NIST recommend following least privilege.
CyberFOX AutoElevate Features
Balance security and work enablement by providing necessary accessibility without allowing unnecessary risk.
- Elevate Privileges for Applications & Actions
- Define Robust Rules for PAM Automation
- Automatic PSA Time Entries
- Detailed Ticketing
- Manage Privileges Remotely
Integrations
Our integrations streamline deployments and workflows without interrupting essential work.
What Our Customers Are Saying
See Our Solutions in Action
Ready to see how easy it is to put our advanced cybersecurity solutions to work for you? Start your free trial or schedule your free demonstration today.
In-Depth Cybersecurity Insights
5 DNS filtering myths (that put users at risk)
Despite all of their cybersecurity benefits, DNS filters remain one of the most misunderstood tools in most IT pros’ stacks..
Is your AI talking to strangers? DNS filters can help
Remember when the biggest threat to an organization’s cybersecurity was someone writing their password on a sticky note? Ah, those.

7 ways DNS filtering keeps users safe (and makes your job easier)
DNS filtering is the unsung hero of cybersecurity. It quietly does the hard work of protecting your network while all.

Why DNS filters should be part of your cybersecurity stack
Let’s be honest, most of us don’t think about DNS (Domain Name System) filters until something goes wrong. This behind-the-scenes.

Why MSPs need to offer password management (before clients ask for it)
You’re already your clients’ go-to person for system updates, troubleshooting, new user onboarding, and everything in between. But if you’re.





